Hello everyone
I am quite new in the Linux world. In Jays book “Mastering Ubuntu Server” there is a chapter about password policies in which he uses libpam-cracklib in the /etc/pam.d/common-password file.
Unfortunately libpam-cracklib does not seem to be available for Debian 12.
After some searching I found libpam-pwquality which can also be used to configure parameters like retry, minlen and difok.
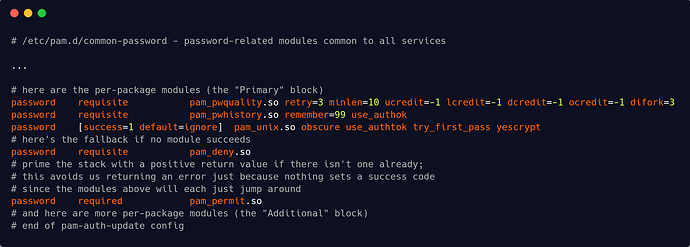
/etc/pam.d/common-password example from the book (with pam_pwquality instead of pam_cracklib)
# This module saves the last passwords for each user in order to force password change history and keep the user from alternating between the same password too frequently.
password required pam_pwhistory.so remember=99 use_authok
#This module can be plugged into the password stack of a given service to provide some plug-in strength-checking for passwords. The code was originally based on pam_cracklib module and the module is backwards compatible with its options.
password required pam_pwquality.so retry=3 minlen=6 difok=3
However, in my search on the Internet I have not found a good template. What should be absolutely in such a password guideline and what should not be done in any case? How is this done in “real use” outside of a home lab?